The CIS Controls: A Way to Meet the NYS OAG Data Safety Tips
Are you a New York business owner? If so, you'll want to check out the guidance outlined in "Protecting consumers’ personal information – Tips for businesses to keep data safe and secure." The New York State (NYS) Office of the Attorney General (OAG) released this document earlier this year to help business owners like you bolster your cybersecurity posture and foster consumer trust. Once lost, after all, it's hard to regain. By prioritizing security, you aren't just investing in complex codes or protective firewalls; you're also investing in the longevity of your brand and your relationship with your customers.
Not to mention, you're protecting your business against potential consequences. Under New York law, businesses must use reasonable safeguards to protect New Yorkers' personal information. When it appears that a business has failed to do so, the Office of the Attorney General will investigate and, if appropriate, take legal action. With this in mind, it's important to follow the guidance of the NYS OAG. But how do you best do this?
 In this blog post, we'll discuss how harnessing the CIS Critical Security Controls (CIS Controls) – a recognized framework for enhancing your cybersecurity program – can help your business meet the NY Attorney General's new tips for keeping data safe while maintaining customer trust.
In this blog post, we'll discuss how harnessing the CIS Critical Security Controls (CIS Controls) – a recognized framework for enhancing your cybersecurity program – can help your business meet the NY Attorney General's new tips for keeping data safe while maintaining customer trust.
Mapping the CIS Controls to the NYS OAG Guidance
First, here's a look at how you can meet some of the recommendations outlined by the NYS OAG by implementing the CIS Controls and their supporting CIS Safeguards.
|
OAG Recommendation |
Mapping to CIS Control and Safeguard |
|
Maintain controls for secure authentication |
CIS Safeguards 5.2, 5.6 |
|
Encrypt sensitive customer information |
CIS Safeguards 3.6, 3.9, 3.10 |
|
Ensure service providers use reasonable security measures |
CIS Safeguards 15.2, 15.4, 15.5 |
|
Know where you keep consumer information |
CIS Safeguards 3.1, 3.2 |
|
Guard against data leakage in web applications |
CIS Safeguards 16.9, 16.10 |
|
Protect customer accounts impacted in data security incidents |
CIS Safeguards 17.4 |
|
Delete or disable unnecessary accounts |
CIS Safeguards 5.3, 6.2 |
|
Guard against automated attacks |
CIS Safeguards 6.3, 6.4, 6.5 |
|
Provide clear and accurate notice to consumers |
CIS Safeguards 17.4, 17.6, 17.8 |
The CIS Controls as Your Cybersecurity Launchpad
With the proactive measures discussed above, you can stay ahead of the cybersecurity curve. Embracing tools and frameworks like the CIS Controls is just the beginning. You can go beyond just adhering to current standards and instead actively engage in cybersecurity dialogue and training, ensuring that you're prepared for what lies beyond the horizon. It's a never-ending journey, one that's essential in the quest to ensure that the digital realm remains a space of trust rather than one of trepidation.
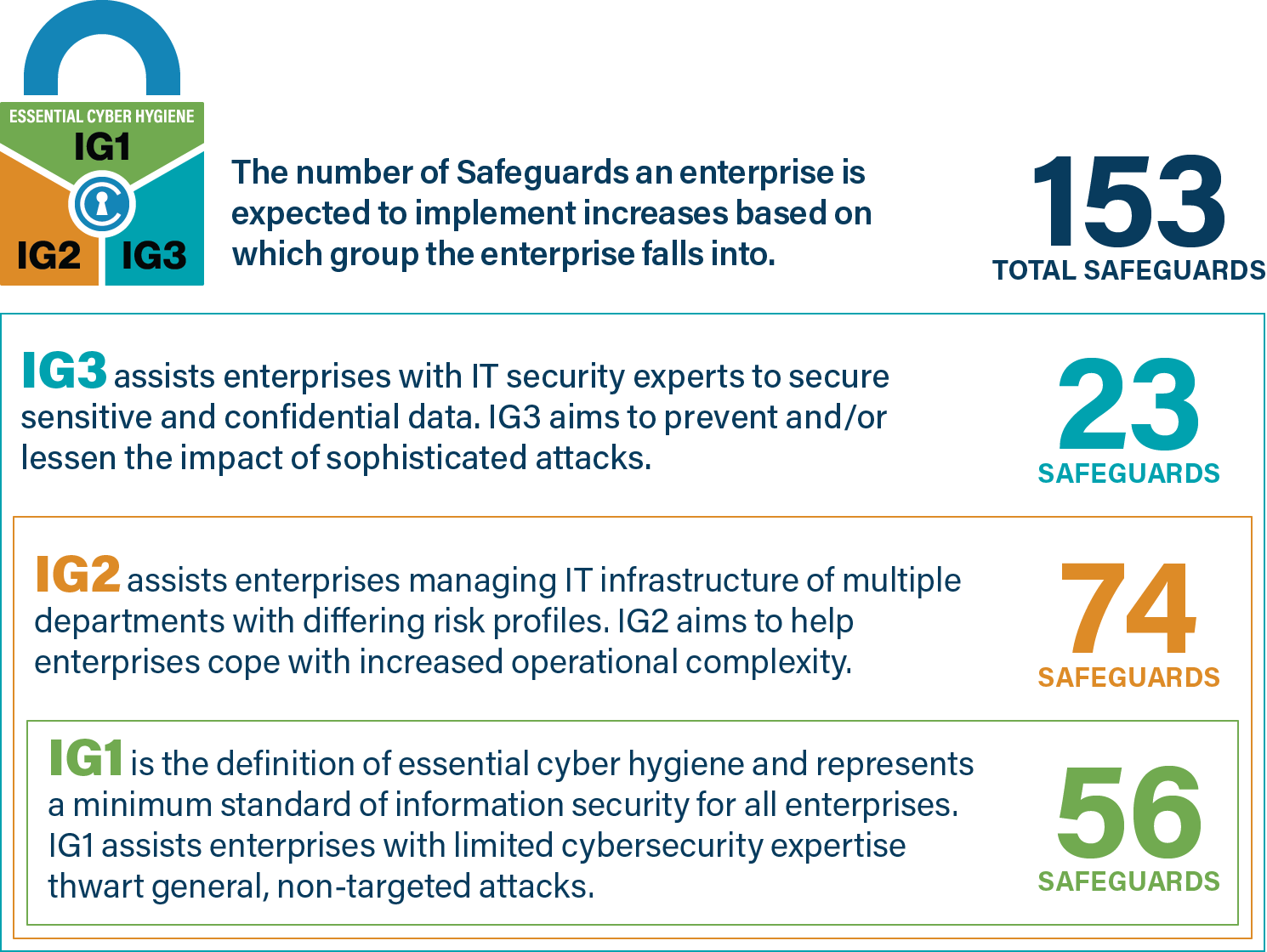
As discussed above, the CIS Controls are very effective in implementing the OAG data security recommendations. If you're new to the CIS Controls, we recommend you adopt CIS Controls Implementation Group 1 (IG1) as a starting point. IG1 is how CIS defines essential cyber hygiene; it represents an emerging minimum standard of information for all enterprises.
Want to learn more how you can use essential cyber hygiene to improve your business's cyber defenses? Check out our video below.
To help you get started with IG1 and strengthening your cyber defenses, we released The Cost of Cyber Defense: CIS Controls IG1. This guide is designed to help you navigate three considerations when it comes to improving your cybersecurity posture: (1) which protections you should start with, (2) which tools you need to implement those protections, and (3) how much implementation will cost. Using this guide, you'll be able to streamline your cybersecurity program so that you can use the resources you need in as efficient a manner as possible.
Start Building Your Robust Cybersecurity Posture Today
The NY Attorney General's tips for data security and the CIS Controls share a common objective: fortifying data protection strategies to safeguard sensitive information. By embracing the CIS Controls, you can establish a robust cybersecurity posture that aligns with the Attorney General's recommendations. This not only enhances security but also contributes to building consumer trust in an era where data breaches are an ever-present concern.
Ready to take your business's cybersecurity maturity to the next level?
